Wolfralyze
Professional Code Quality Analysis for Wolfram Mathematica™
The industry's FIRST and ONLY Tier 1 SonarQube® plugin for Wolfram Mathematica™
Professional Code Quality Analysis for Wolfram Mathematica™
The industry's FIRST and ONLY Tier 1 SonarQube® plugin for Wolfram Mathematica™
Wolfralyze brings enterprise-grade code quality analysis to Wolfram Mathematica™, matching the depth and sophistication of analysis available for Java, Python, and other mainstream languages.
Wolfralyze provides best-in-class support for Wolfram Mathematica™, comparable to SonarQube® support for major programming languages:
| Feature | Java | Python | Mathematica™ |
|---|---|---|---|
| Rules | 733 | 410 | 559 |
| AST Parser | ✅ | ✅ | ✅ |
| Symbol Table | ✅ | ✅ | ✅ |
| Type System | ✅ | ✅ | ✅ |
| Data Flow | ✅ | ✅ | ✅ |
| Taint Analysis | ✅ | ✅ | ✅ |
| Test Coverage | ✅ | ✅ | ✅ |
| Quick Fixes | ✅ | ✅ | ✅ |
Comprehensive code quality analysis for Wolfram Mathematica, integrated seamlessly into SonarQube.
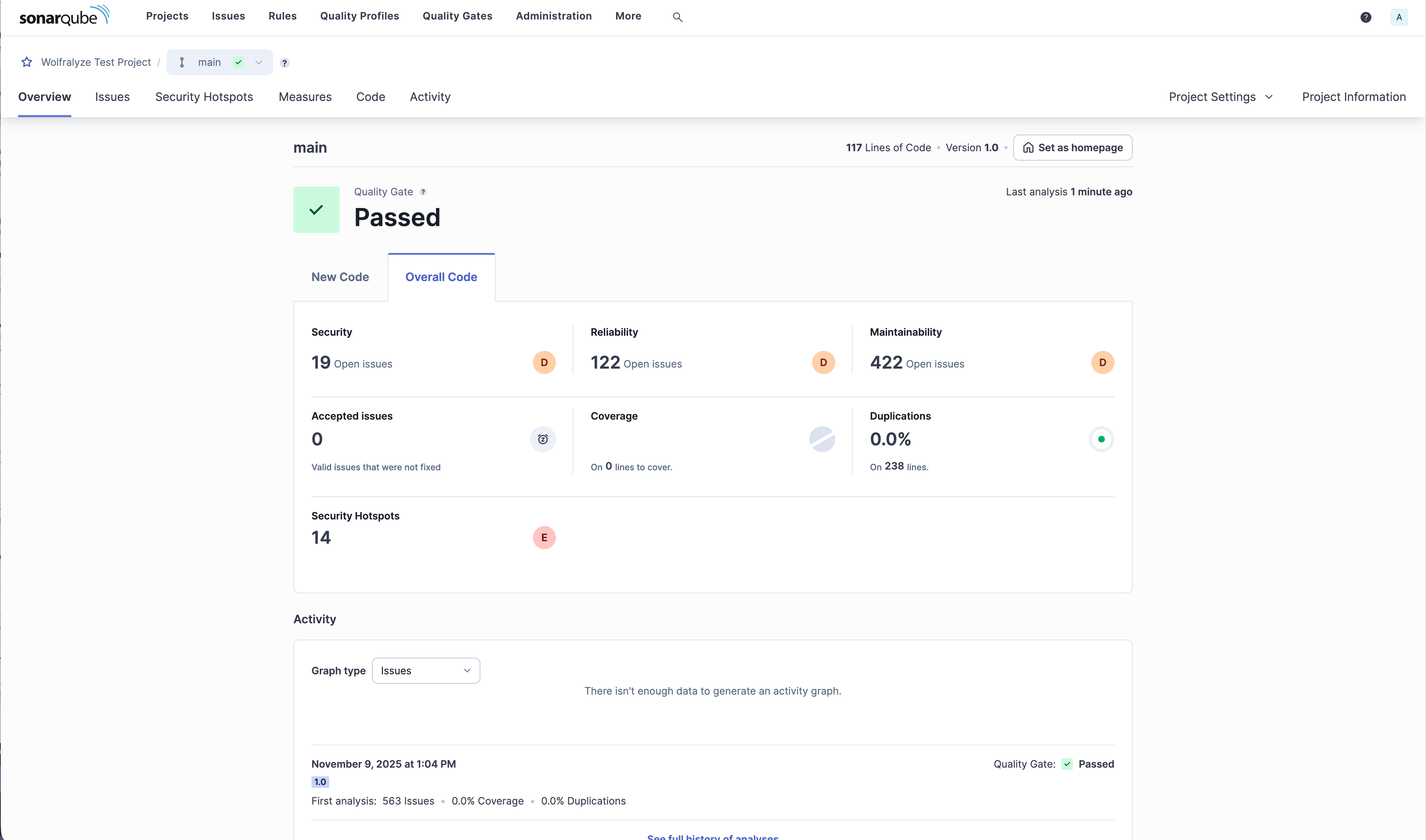
Real-time quality metrics for your Mathematica projects with bugs, vulnerabilities, and code smells clearly displayed.

Comprehensive issue list showing security vulnerabilities, bugs, and code smells with severity indicators.
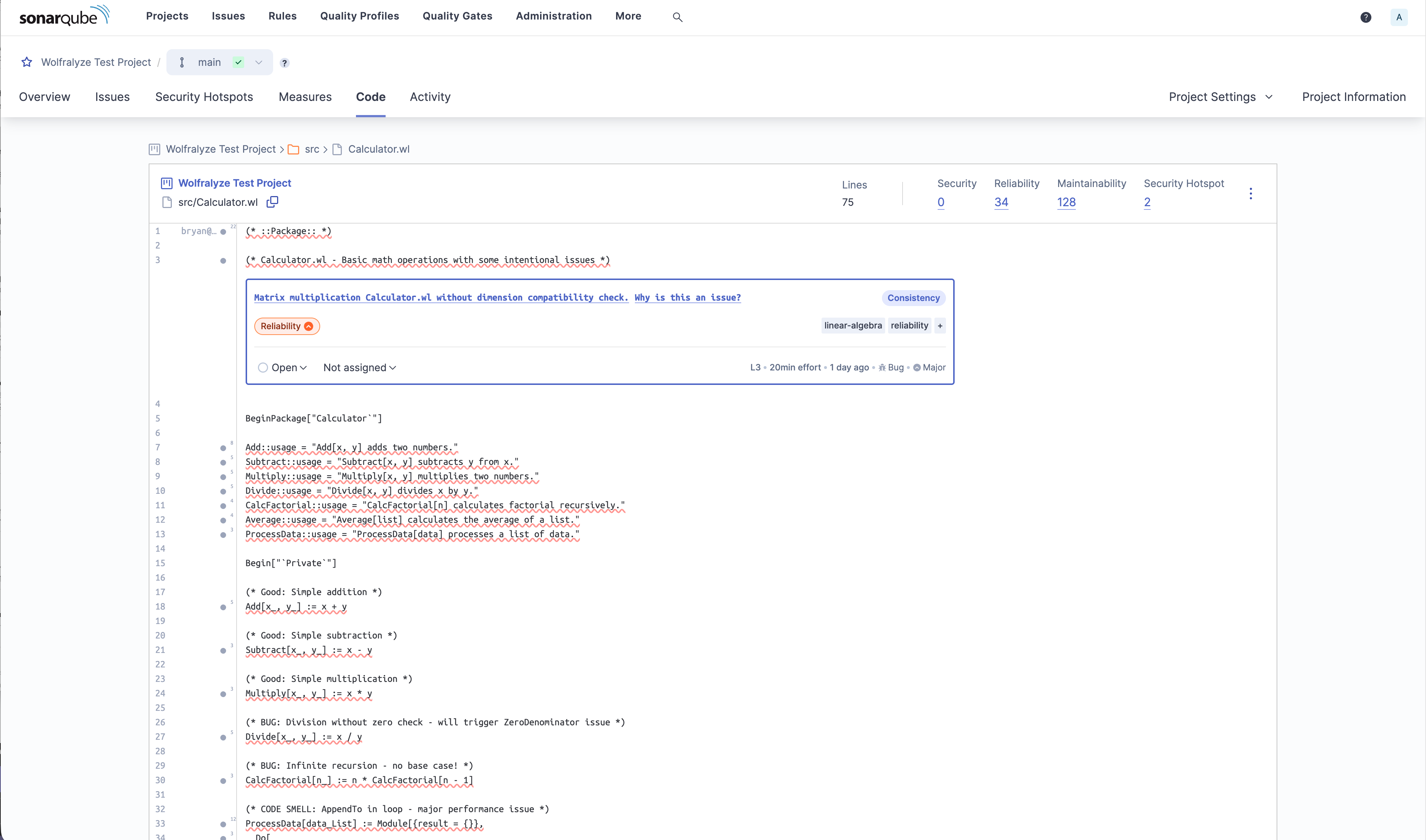
Mathematica code with full syntax highlighting and issues highlighted directly in the source.
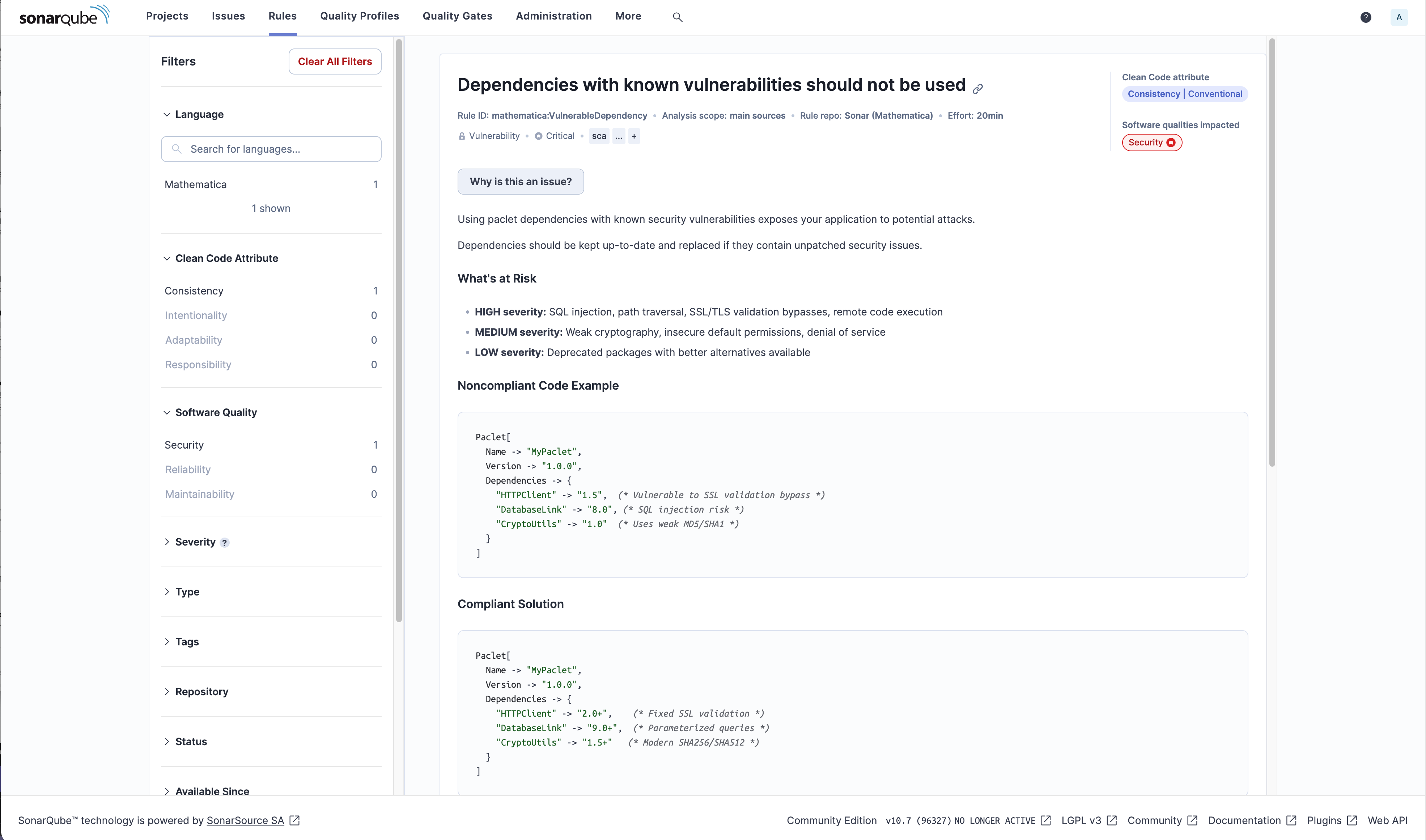
Detailed explanations for each rule with examples and remediation guidance specific to Mathematica.
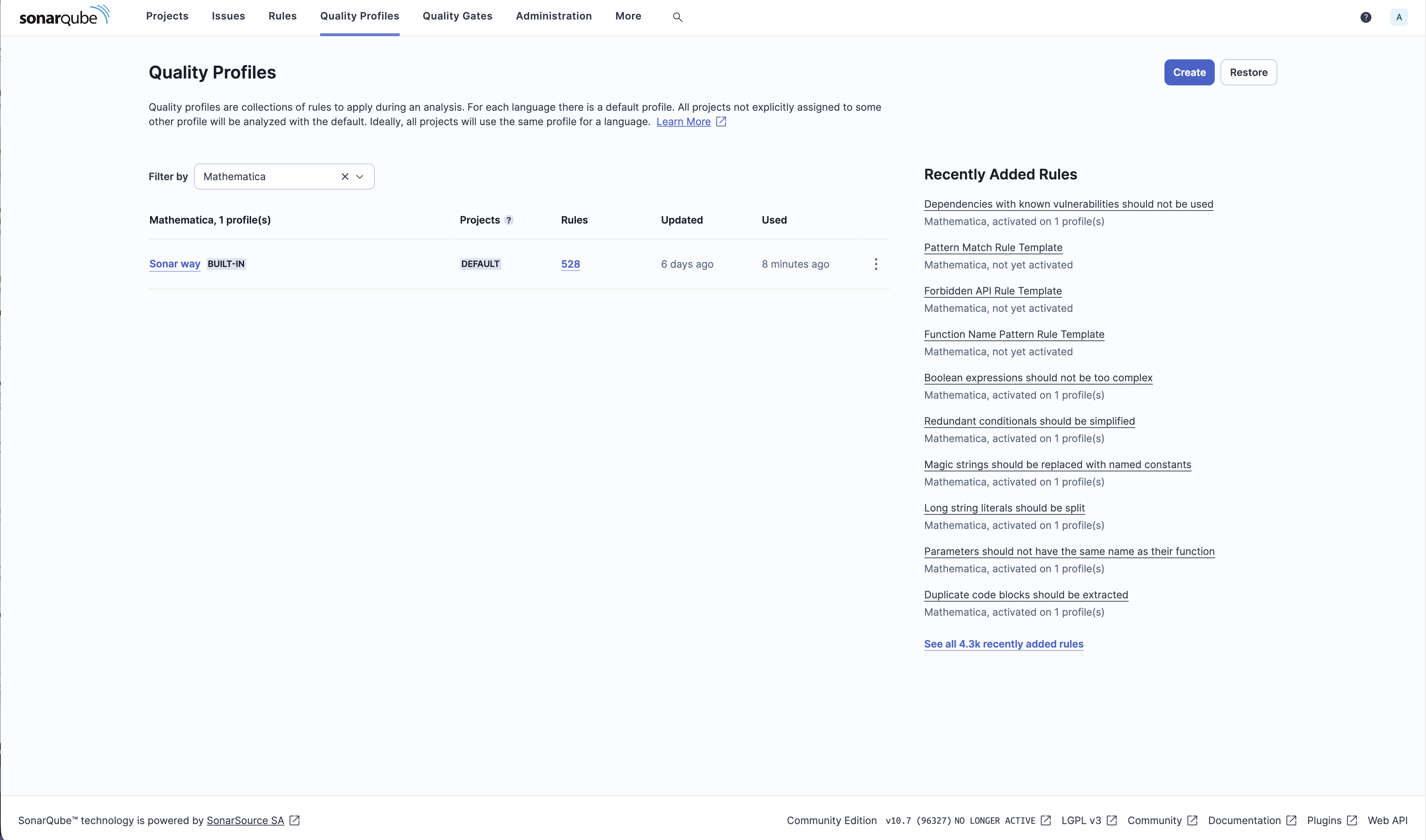
559 rules organized by type: bugs, vulnerabilities, security hotspots, and code smells, including 21 coding standards.
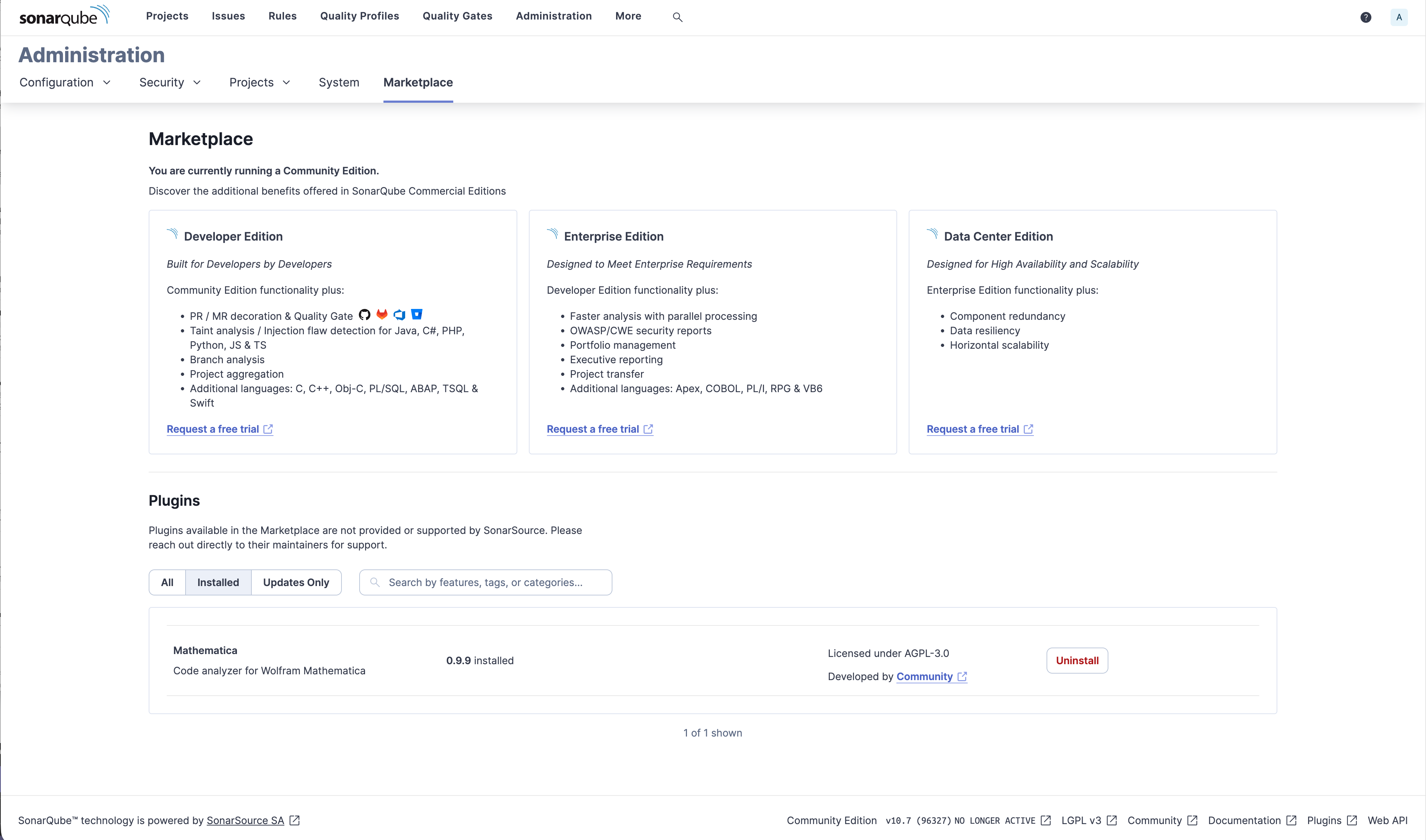
Plugin installs cleanly into SonarQube and appears in the marketplace with full metadata.
Screenshots show Wolfralyze analyzing the test project with intentional code quality issues.
# Download the latest release
curl -L -o wolfralyze.jar \
https://github.com/bceverly/wolfralyze/releases/latest/download/wolfralyze.jar
# Copy to SonarQube plugins directory
cp wolfralyze.jar $SONARQUBE_HOME/extensions/plugins/
# Restart SonarQube
$SONARQUBE_HOME/bin/[platform]/sonar.sh restart# Create sonar-project.properties in your project root
cat > sonar-project.properties << EOF
sonar.projectKey=my-mathematica-project
sonar.projectName=My Mathematica Project
sonar.sources=.
sonar.inclusions=**/*.m,**/*.wl,**/*.wls
EOFsonar-scannerOpen your browser to http://localhost:9000 and see: